Your identity blind spots end here.
Siloed visibility and rubber-stamped reviews shouldn't be the norm. Oleria ends the identity guessing game with a fine-grained, usage-aware access graph that covers all types of identity. Finally, you can see and control identity access across every system.

Built by practitioners. Trusted by security leaders worldwide.

Identity security needs a reset
Fragmentation leaves you guessing
Your IdPs, custom apps, cloud, and HR systems all have their own language on identity and access. Siloed data leaves you with fragmented identities. By the time you manually connect the dots, the landscape has completely changed.
Seeing permissions isn't enough
Permissions and entitlements show who can access your systems — but not what they’re doing with that access. That gap fuels risk, wasted spend, and endless “check-the-box” compliance cycles.
Oleria’s Trustfusion Platform
Full clarity to monitor, manage, and act—faster.
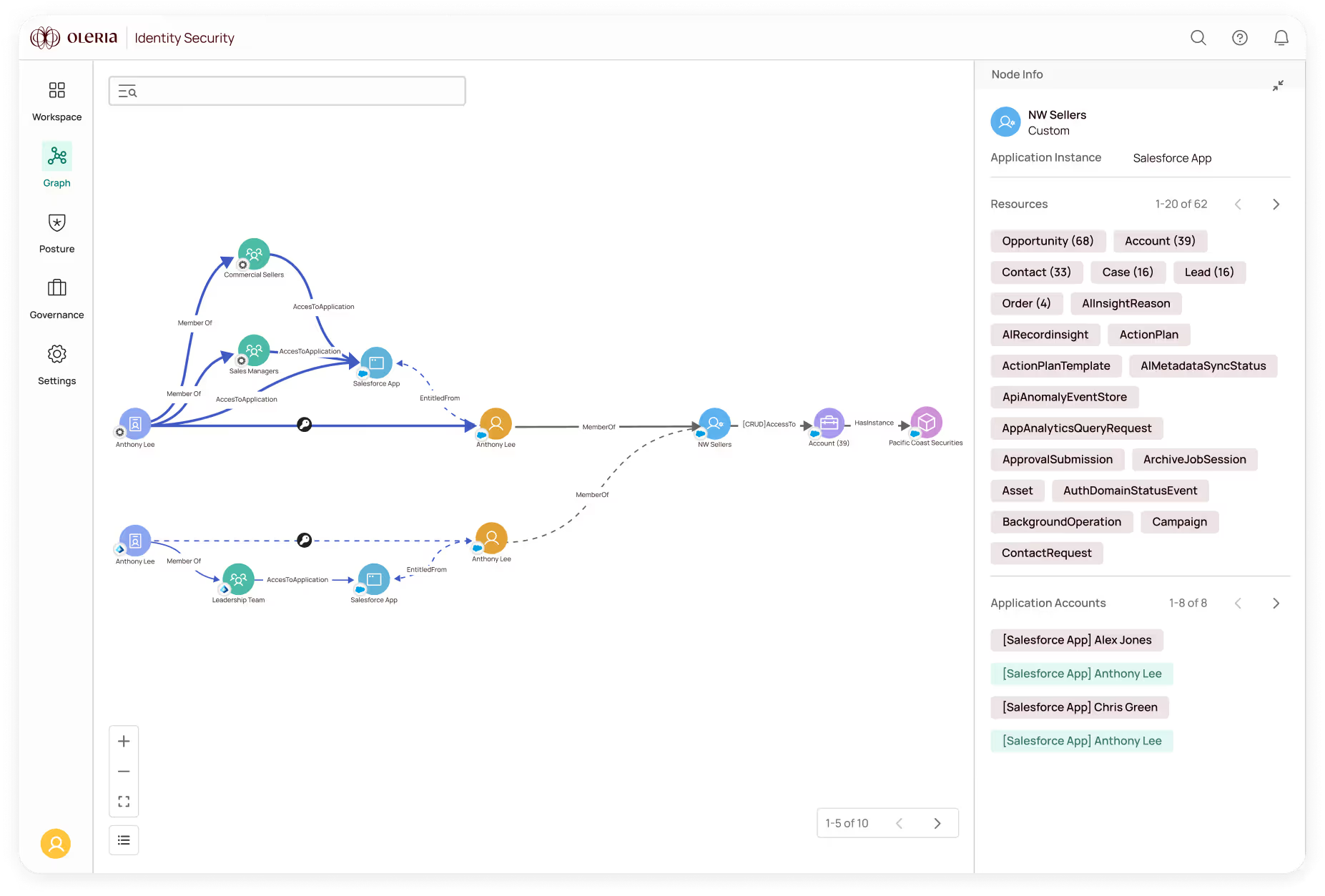
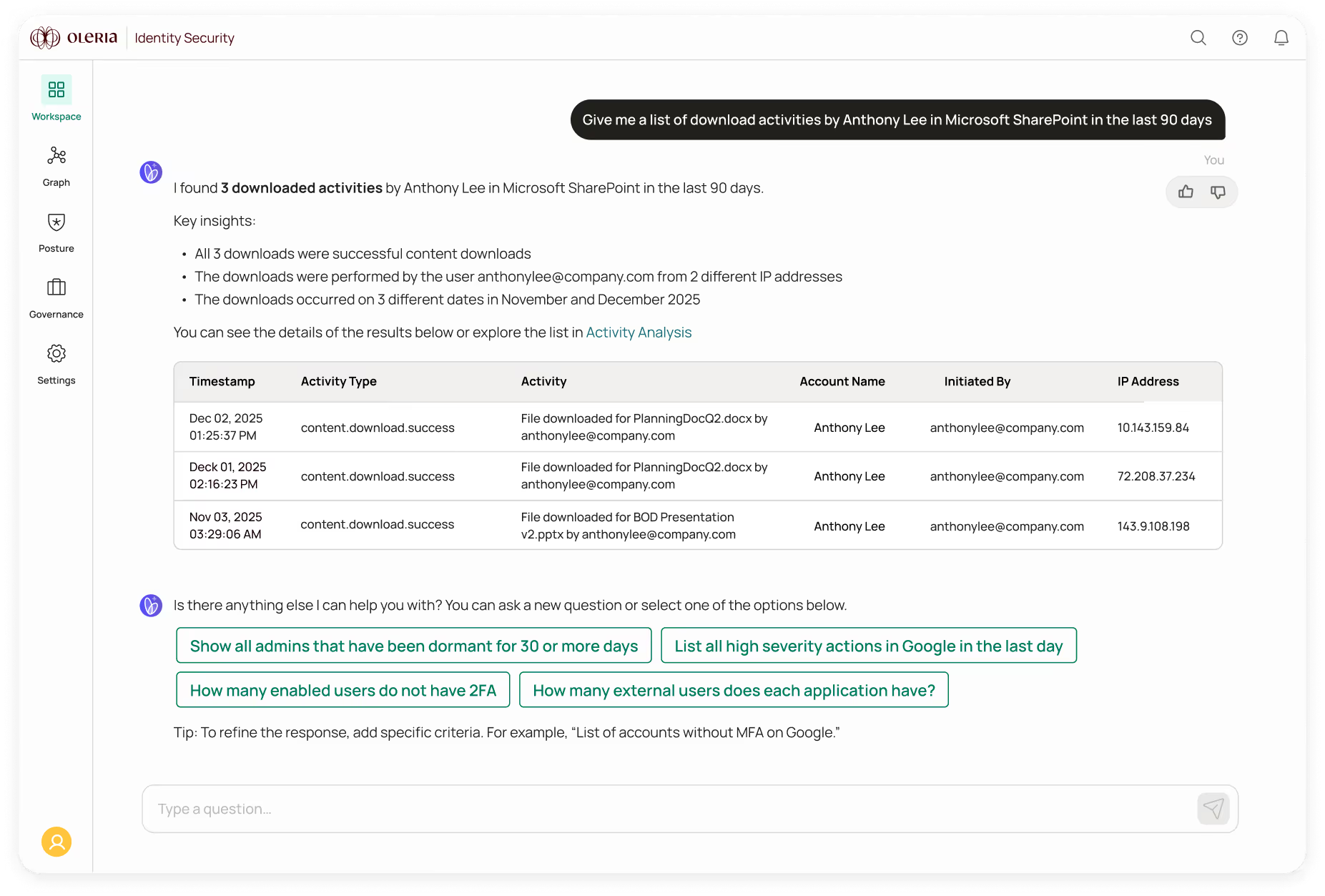
Oleria unifies fragmented identity and access data to give you the single, consistent view you’ve always wanted. We go deeper than permissions, revealing usage-level data down to the individual resource so you can see what’s actually happening across your environment.
.avif)
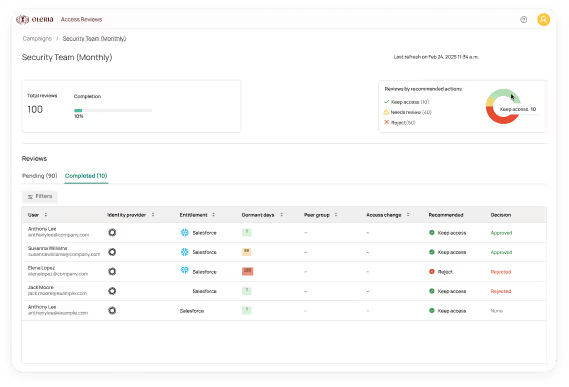
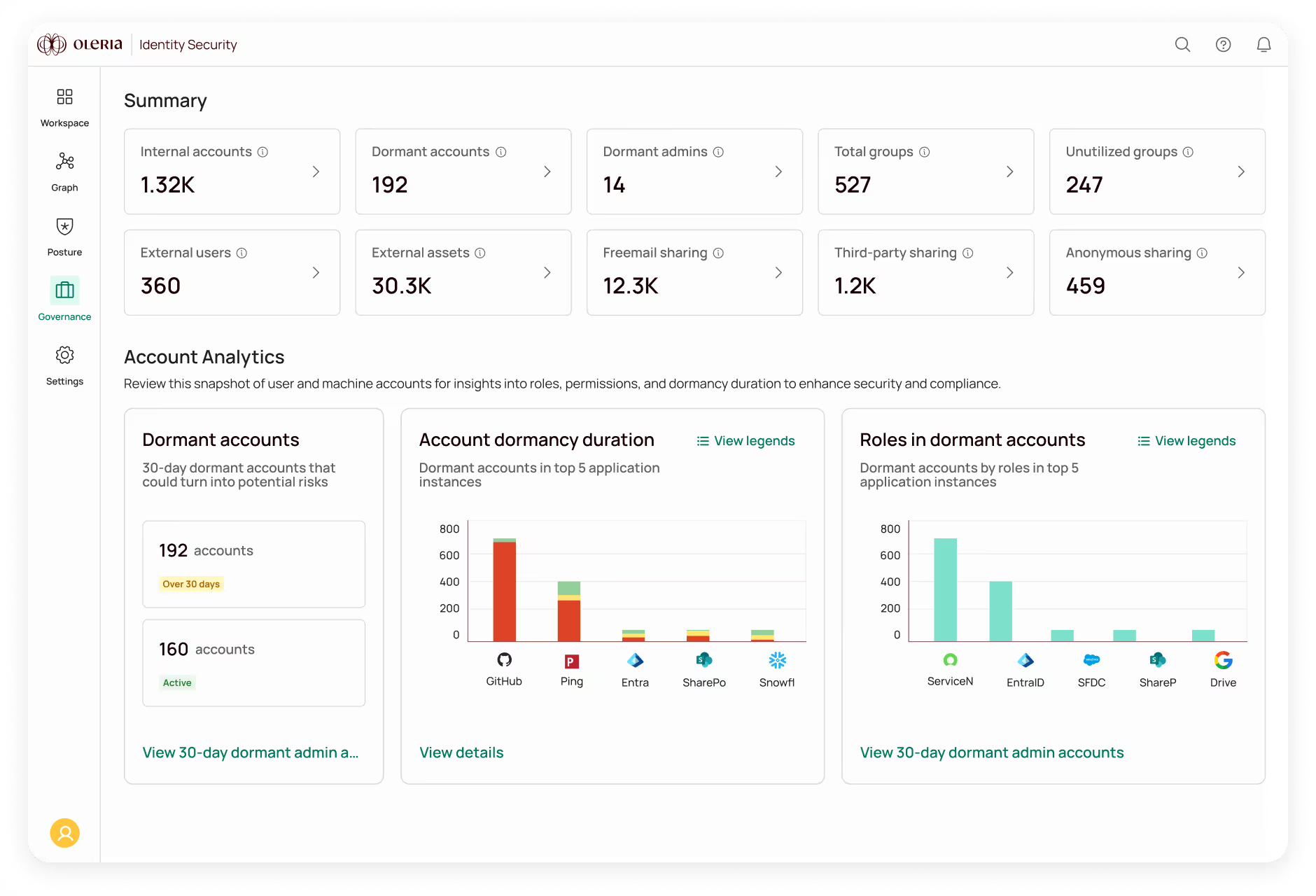
See dormant accounts and unused access.
No more “swivel chair” manual work across identity silos. Oleria unifies human, non-human and AI identity data from IdPs, SaaS, cloud, HR, and custom systems and enriches it with activity insights – giving you precise visibility across your environment.
Continuously enforce least privilege.
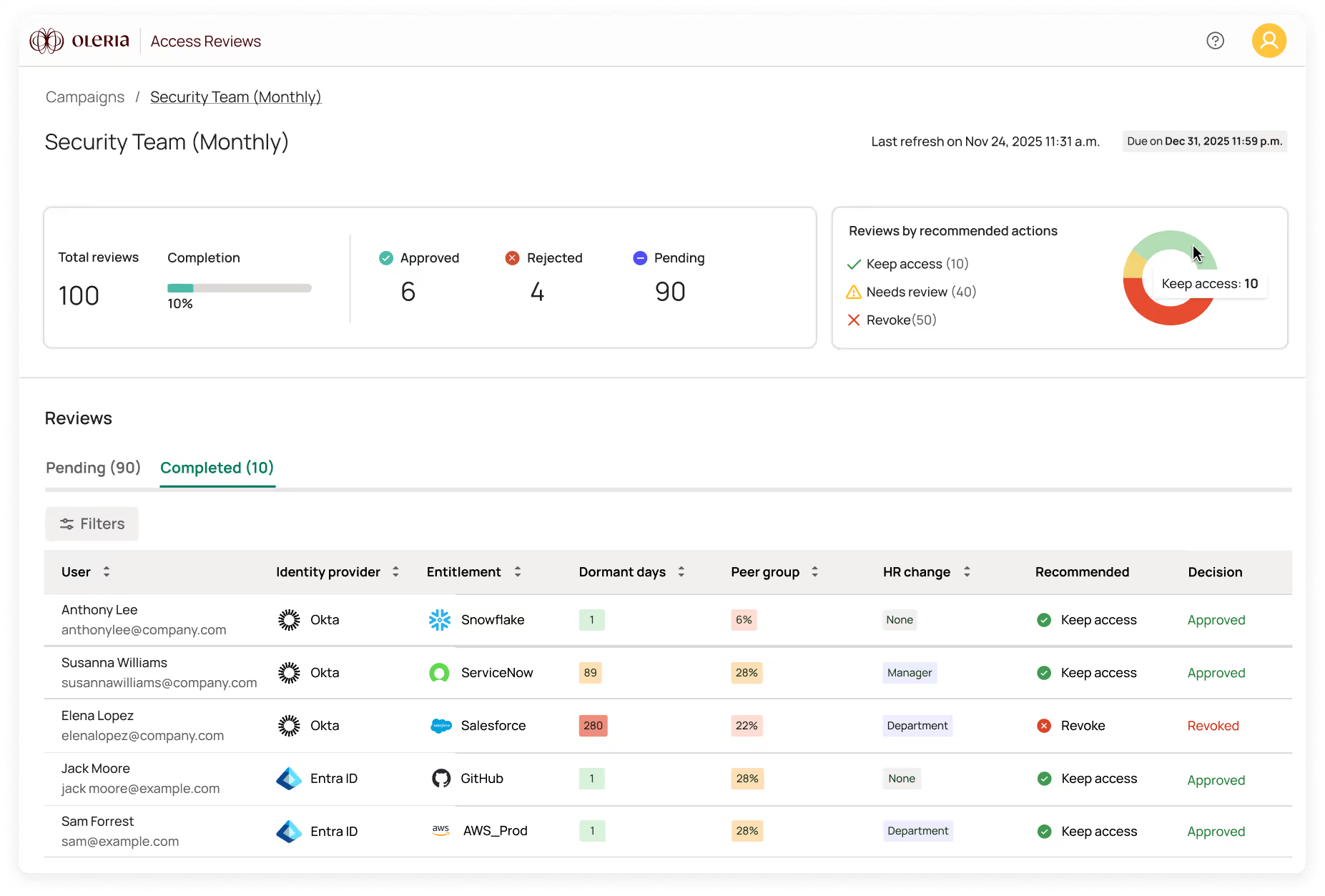
Stop rubber stamping and start making access reviews matter. Oleria’s AI-driven intelligence streamlines access reviews, lifecycle management, and compliance reporting so you can continuously enforce least-privileged access.
Revoke access in seconds, not weeks.
Insight without action only adds to alert fatigue. Oleria helps you act fast with AI-powered, prioritized remediation that’s fully tracked, auditable, and reversible for total confidence.
.svg)

The implementation story no one believes (until they see it)
“I can imagine using Oleria without using Okta or SailPoint — but I can't imagine using those two tools without using Oleria moving forward… Within 45 minutes of the first login, we saw a robust picture of accounts and access across our organization that we could immediately begin remediating.”
.svg)
.svg)

Unparalleled visibility into identity access and usage
“Oleria provides MTX and our customers with unparalleled visibility into identity access and usage. From ensuring readiness for AI deployments to shoring up Salesforce security to saving time and money on IGA deployments, Oleria has been an invaluable partner.”

Built by practitioners — for practitioners
Designed for the people who secure the enterprise.
Oleria was created by security leaders who’ve lived the pain of fragmented IAM, endless audits, and blind-spot risks. We built what we always needed: clarity, automation, and control that secures the business without slowing it down.
CISOs
Gain unified visibility and AI-driven intelligence to strengthen posture, demonstrate compliance, and drive proactive security programs.
Security Operations
Accelerate detection and response with fine-grained insights, automated remediation, and continuous monitoring across every identity.
Director of IAM
Eliminate identity silos, enforce consistent policy, and hand off clean, reliable data to GRC with Oleria’s precise, unified, usage-aware identity visibility.
GRC & Compliance
Automate evidence collection and access reviews to simplify audits and maintain continuous regulatory alignment.
We did the hard work so you don’t have to.
No heavy lift. No custom code. No waiting.
Active Directory
SuccessFactors
OneDrive
Oleria built deep integrations that go beyond permissions and entitlements to pull identity data at the resource and usage level — and normalize that fine-grained, usage-aware data into a single, common schema. This is your key to least privilege access at the resource level and the foundation for managing identity in the age of AI.
The result: Customers typically gain actionable insights within an hour of deployment.
Resources
Insights for identity-driven enterprises
Managing Identity in the Age of AI
Identity will secure and enable – or inhibit – tomorrow’s AI-fueled business world. Get the guidance you need to prioritize investments and allocate resources to best manage identity-related risk.

.avif)


.avif)