Blog
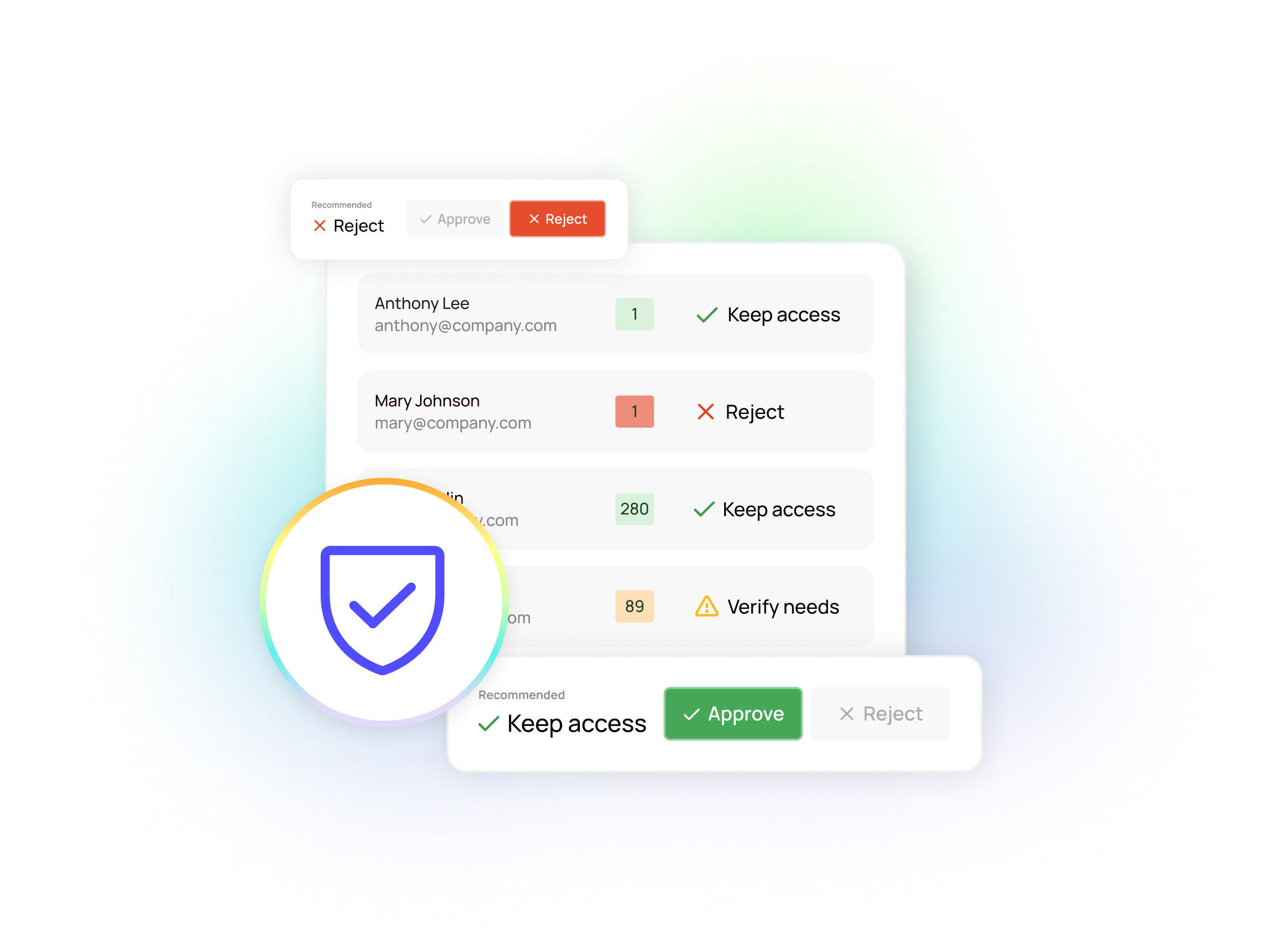
Access reviews are broken, but they don’t have to stay that way
Access reviews serve a critical purpose: they’re the backbone of least-privilege security, ensuring that people have exactly the access they need, no more and no less.
But most organizations don’t experience access reviews that way. Instead, security teams, IAM teams, GRC teams, and managers struggle with review cycles that are slow, opaque, and missing the context needed to fully understand access and make confident decisions. Managers, in particular, are asked to balance security with business continuity — yet are forced to make these high-impact choices without the right data to weigh the business risk of approving access against the business impact of removing access.
So, reviewers end up choosing between two imperfect options: approve access they can’t fully validate, or revoke access that might be essential for productivity. Given the stakes, most reviews ultimately default to rubber-stamped approvals.
It’s a system that everyone knows is broken, but most have accepted as unfixable. Until now.
The reality: access reviews are performed in the dark
On paper, access reviews provide a structured and repeatable process for regularly validating user access privileges. In practice, most organizations run head-first into the same set of problems the moment they launch an access review campaign:
- Time-consuming manual reviews. IT and security teams spend countless hours manually consolidating access across multiple systems, applications, and cloud platforms, and then associating access to individual employees. Then, they spend more time doing individual access reviews. For large organizations, a single review cycle can take months, creating reviewer fatigue and serious operational overhead.
- Lack of the right data (contextual information). Reviewers are often looking at permissions and group memberships, but rarely see the context they need to assess risk and confidently determine whether access is still appropriate. They can’t easily see how frequently access is used, whether peers in similar roles have the same entitlements, or whether a user’s role or department has recently changed. Without this context, reviewers understandably hesitate to revoke anything that isn’t obviously incorrect.
- Review experience that doesn’t match how managers think. Business approvers are asked to review long lists of technical or opaque entitlements in interfaces that don’t match how they think about their teams’ work. It’s something they’re doing on top of their real job, so it’s no surprise they rush through it accordingly.
Put simply, reviewers are asked to make high-impact decisions with low-quality information. The result? They rubber-stamp anything that looks "normal" and question only the obvious outliers. Or, worse, they abandon the review process altogether, creating bigger compliance issues down the road.
Why this has felt like an intractable problem
If the experience is so clearly and familiarly flawed, why has the industry tolerated this status quo? The root of the issue is that cross-system access correlation and visibility has been almost impossible to achieve in practice. Identity and access data is fragmented across identity providers (IdPs), SaaS apps, cloud and on-prem systems, HR data, and security logs. All of which use different schemas and different “languages” for describing access.
And legacy IGA tools add to the challenge. They were largely built for IT administrators, not for the managers, IAM teams, and GRC stakeholders now responsible for approving access.
Stakeholders know this isn’t ideal. But they also know that digging to get that deeper context isn’t practical. By the time they finish the manual work of correlating access across systems, and pinging application owners and individual employees, the access landscape has already changed.
All of this has led many organizations to accept that access reviews are more of a compliance checkbox than a true risk-reduction mechanism.
What’s been missing: unified, usage-aware visibility + intelligent recommendations
To make access reviews effective, organizations need more than a list of applications and roles that users have access to. They need a single view of user access to all cloud apps, on-prem systems, and IdPs, enriched with actual user activity, peer patterns, and HR context such as role and department changes.
And, perhaps most importantly, they need that unified visibility combined with intelligent, usage-aware recommendations. Without both, reviewers are left to guess.
This is the gap Oleria set out to close.
Oleria’s intelligent Access Reviews: context-first by design
We started by asking how we could give reviewers the information they need to confidently right-size access (instead of rubber-stamping). And how could we do it with the speed and scale to be practical (instead of manual correlation)?
The answer is two-fold:
- One composite access graph, enriched with usage insights.
Oleria breaks down silos to provide a single view of user access across your digital estate, including cloud, SaaS, on-prem, and multiple IdPs. We unify accounts, groups, roles, permissions, and resources into a composite access graph that provides a unified data platform. This is the foundation.
- Intelligence-powered recommendations.
On top of that data, Oleria elevates access reviews with intelligent recommendations. Reviewers see a recommendation on whether a review needs to be approved or rejected, along with the supporting contextual data on why this recommendation was made — context like:- Has this access been frequently used?
- Do similar peers have the same access?
- Did the user just change role or department?
- How has this access been reviewed in the past?
Solving pain points for reviewers and admins alike
With these two components working together, Oleria’s intelligent Access Reviews are helping the people on both sides of the access review process: the managers making decisions and the admins orchestrating the governance program.
- Clarity and confidence for reviewers: Business approvers finally get what legacy systems never provided: clear, usage-aware context behind every entitlement. Instead of staring at opaque permissions, reviewers see real activity with peer comparisons and HR context that make approvals and revocations fast and confident rather than risky guesswork. Moreover, they get intelligent recommendations on whether a review should be approved or rejected — with rich context on why — so there’s no more rushed rubber-stamping simply because the data isn’t there.
- Control and automation for admins: For administrators, Oleria completely redefines the entire review process. From the very start, Oleria helps admins determine which reviews to start first, selecting employees based on different employee attributes that may make their access higher-risk. Admins can modify existing access review campaigns midstream — changing end dates, reassigning, sending reminders, and/or escalating when needed. When the review is complete, instead of isolated, entitlement-by-entitlement changes, Oleria evaluates the entire campaign holistically. This ensures that removing a user from a group doesn’t leave hidden privileges behind — or, conversely, that it doesn't negatively impact productivity downstream by taking away needed access. For organizations that prefer manual interventions, Oleria integrates easily with ticketing systems, so IAM teams can route actions through existing workflows.
In short, Oleria gives admins the precise governance and control (through safe automation or intuitive manual workflows) that they never had with traditional review tools.
“Managing Entra-based access reviews without HR integration is a recipe for blind spots, delays, and unnecessary risk. Oleria’s Access Reviews eliminate that chaos. It delivers the critical context Entra lacks—identity intelligence, real activity data, and peer-group insights—so reviewers can make fast, informed, defensible decisions. Even better, they can instantly remediate risky access and shrink the attack surface in real time. Oleria turns a fragmented, high-friction process into a streamlined, intelligent, and genuinely secure experience for the entire organization.”
- Pete Clay, CISO, Aireon
Compliance readiness without the scramble
Finally, Oleria drastically reduces the compliance burden that has historically accompanied access reviews. At the close of every campaign, Oleria automatically generates complete, auditor-ready reports, including reviewer decisions, contextual justifications, and all remediation actions taken. Teams that once dreaded evidence collection now have clean, comprehensive documentation delivered as an inherent output of the review process.
This dramatically improves operational efficiency and removes the stress associated with proving compliance for frameworks such as SOX, HIPAA, or GDPR.
Putting it all together: Access reviews that accelerate innovation
For individual reviewers and admins, Oleria is solving longstanding pain points in the access review process. But at a broader, business level, Oleria is helping organizations turn access reviews into a process that adds to business speed, agility, and innovation, rather than impeding it.
With unified visibility, usage-aware intelligence, and safe, granular remediation, access reviews become a strategic security control that actually reduces risk instead of just documenting it. Reviewers can quickly validate whether access is appropriate based on real activity, revoke what’s unnecessary with confidence, and keep what’s essential without fear of disrupting collaboration, innovation, or operational velocity.
Instead of slowing teams down, access reviews become a catalyst for moving faster. IAM and GRC teams can strengthen security posture while giving leaders the confidence to accelerate modernization, adopt AI safely, and support the pace of the business.
.png)
Built for the AI Era: How Oleria’s Unified Identity Security Approach Is Validated by the Industry
.png)
Built for the AI Era: How Oleria’s Unified Identity Security Approach Is Validated by the Industry

Access reviews are broken, but they don’t have to stay that way

Access reviews are broken, but they don’t have to stay that way

How Oleria's Trustfusion Platform accelerates identity maturity

How Oleria's Trustfusion Platform accelerates identity maturity
.png)
Managing Identity in the age of AI
.png)
Managing Identity in the age of AI
.png)
Our vision for the future of identity security? It’s already in motion.
.png)
Our vision for the future of identity security? It’s already in motion.
.png)
Solving the non-human identity (NHI) crisis with Jim Alkove and Garrett Bekker
.png)
Solving the non-human identity (NHI) crisis with Jim Alkove and Garrett Bekker

A CISO’s take: Enterprise copilot risks with Jim Alkove and Ramy Houssaini

A CISO’s take: Enterprise copilot risks with Jim Alkove and Ramy Houssaini
.png)
2025 RSAC insights: the rapid rise of autonomous identity security
.png)
2025 RSAC insights: the rapid rise of autonomous identity security

Why I am betting on Oleria as the future of identity security

Why I am betting on Oleria as the future of identity security

Google Workspace security best practices: file-sharing

Google Workspace security best practices: file-sharing

.avif)
