Identity security at AI speed and enterprise scale.
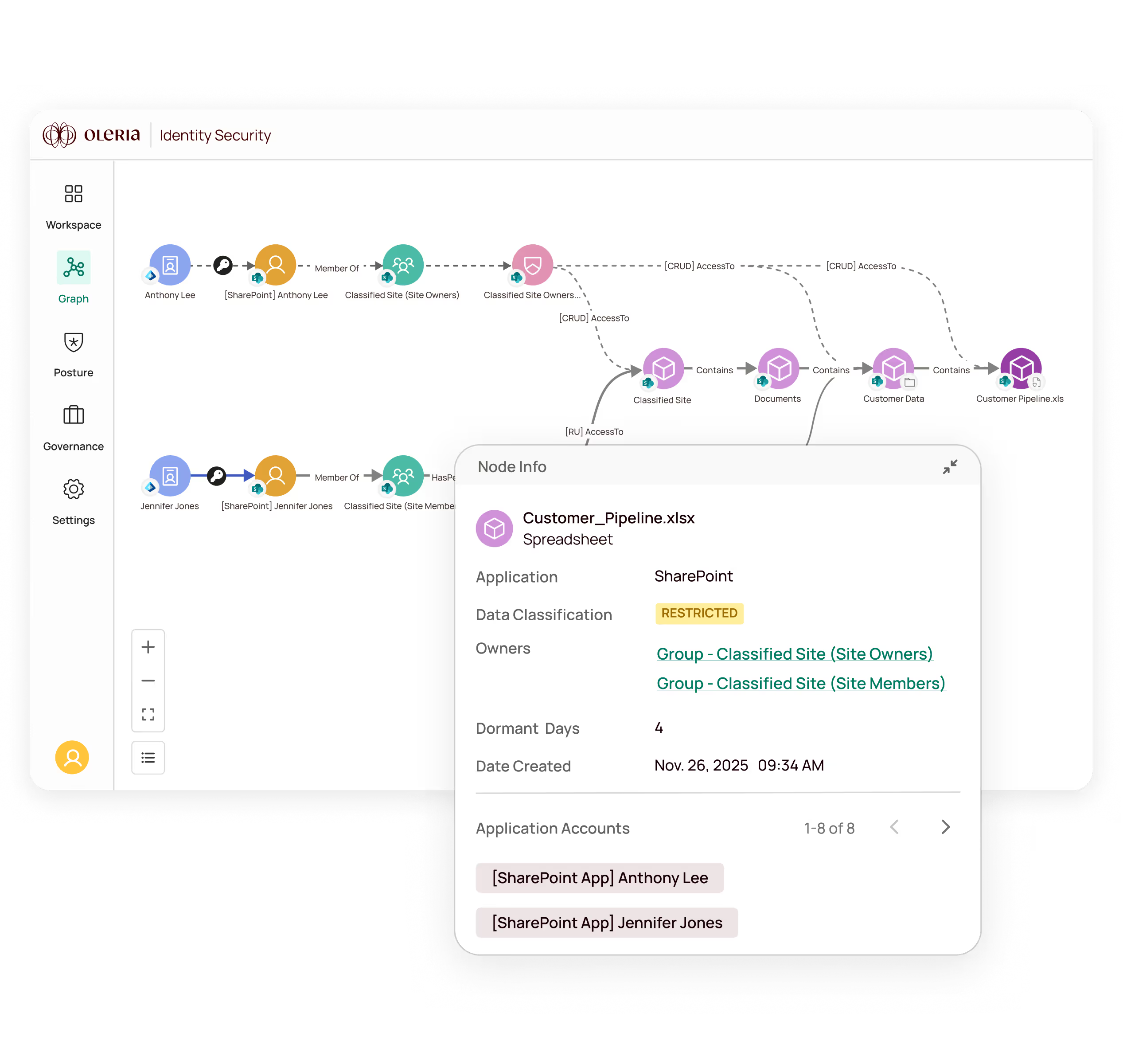
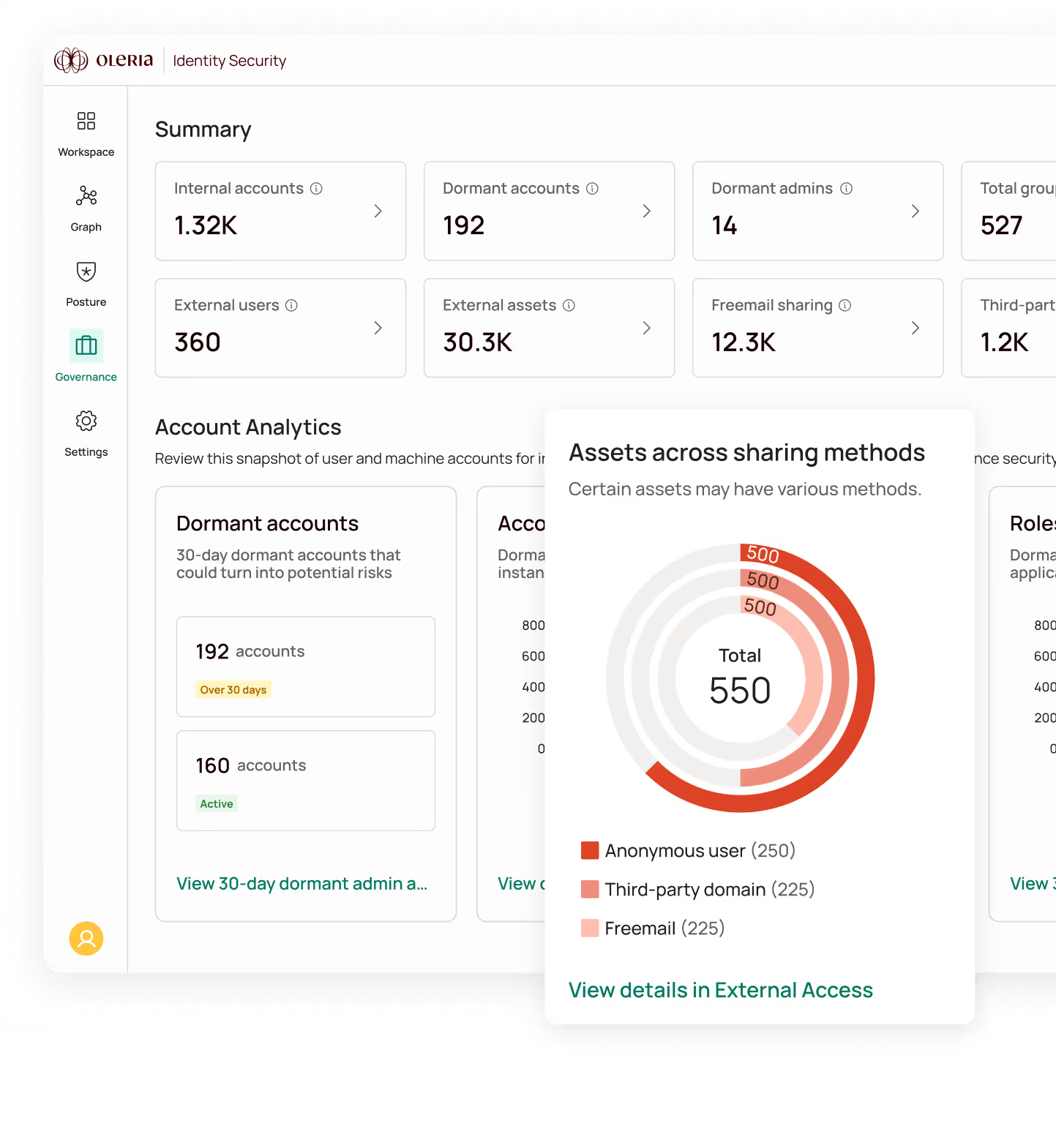
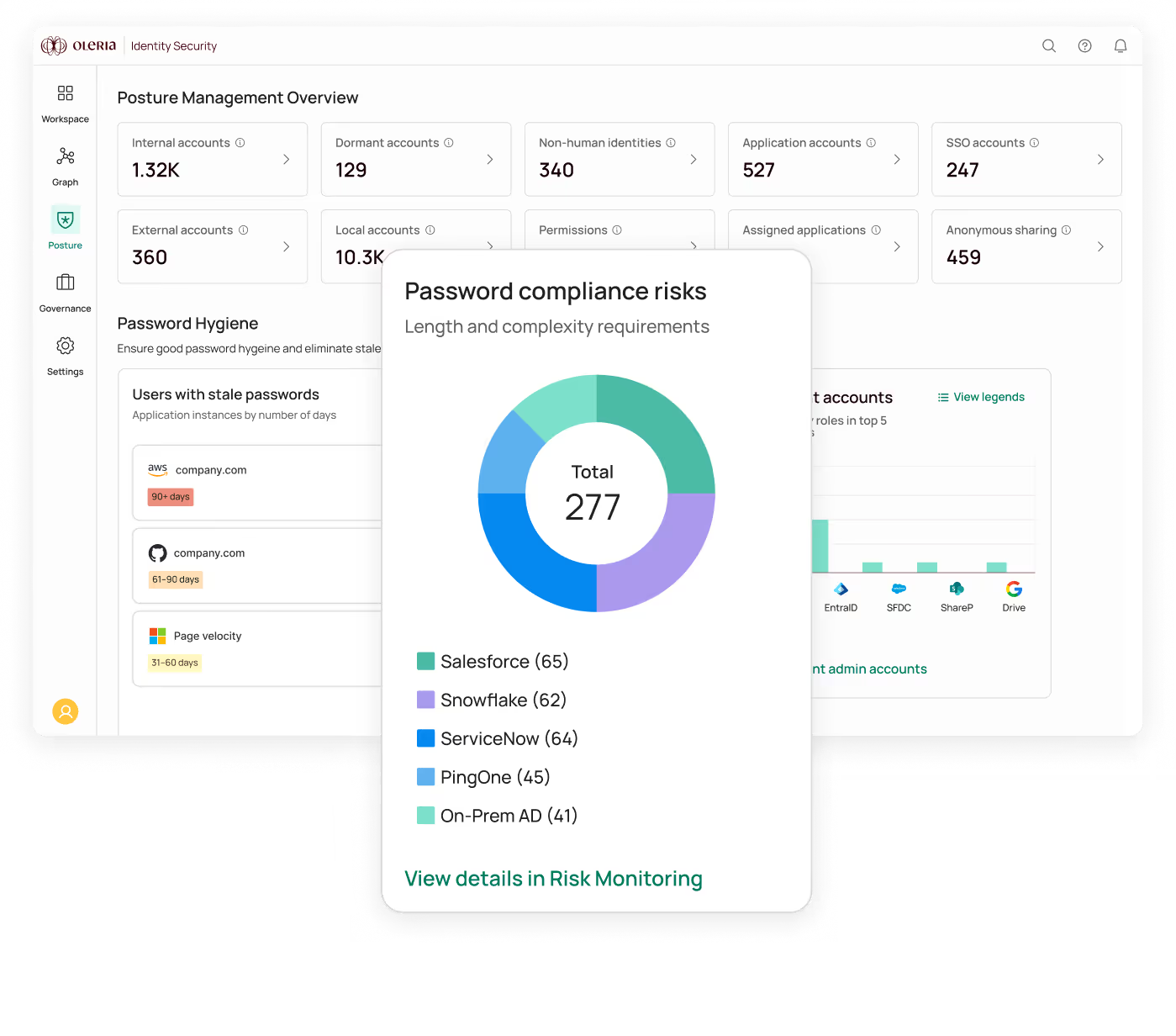
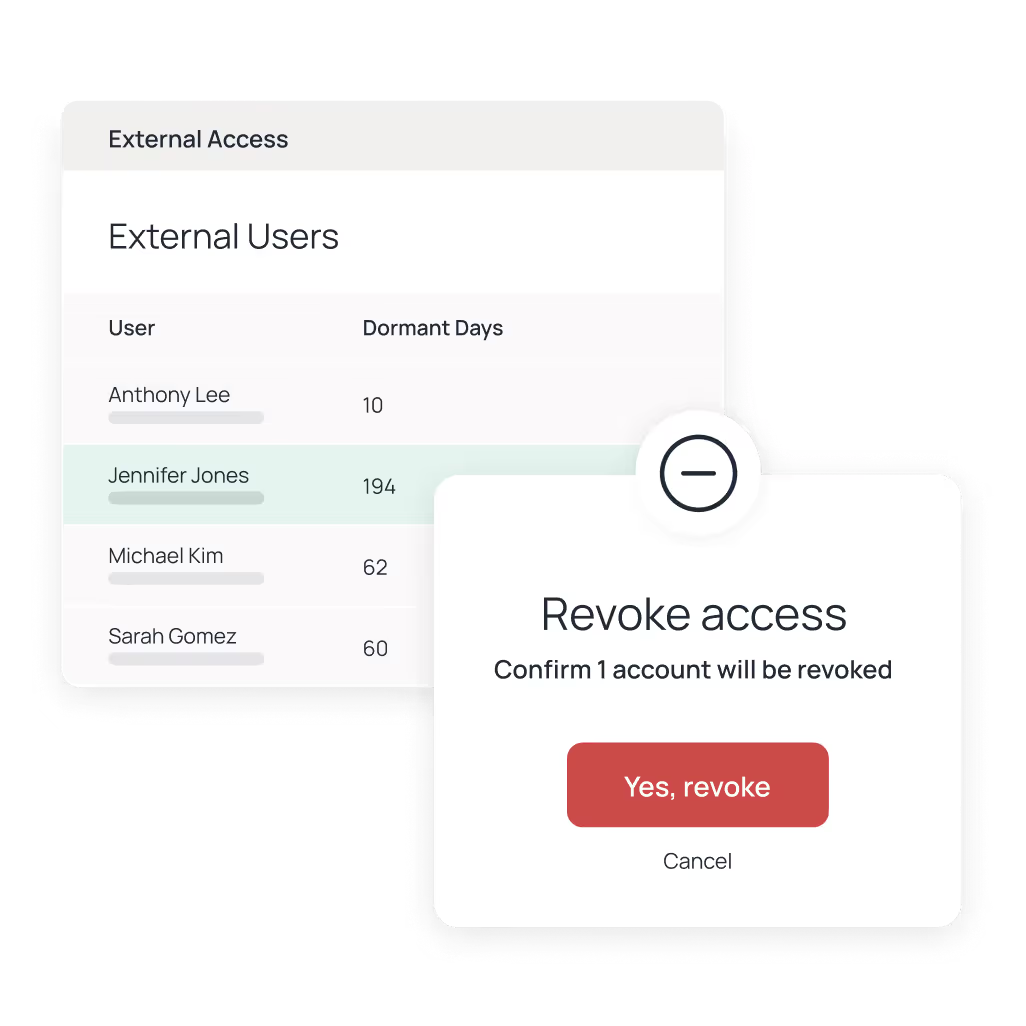
Oleria Identity Security rapidly reveals the 95% of unused permissions1 that present the biggest risk behind today’s identity attacks, giving you fine-grained visibility and control across human, non-human, and AI identities in SaaS, cloud, hybrid, and on-prem environments.
.svg)

.avif)
.avif)
.avif)
.avif)


.svg)
.svg)